Over the past few weeks many organisations will have found themselves implementing their Business Continuity Plans (BCP) - trying to keep their operations running, while the pandemic impacts their supply chains, workforces and operations.
And for some, this may have been a rude awakening to the shortcomings in their preparation. For others, it might have highlighted opportunities to improve their plans. Not only to mitigate the risk of future events, but also to prepare for how the current pandemic may evolve.
One particular challenge for businesses as they implement their BCP, is ensuring cyber security is properly considered, and their critical systems and data remain protected.
In their haste to implement remote working for example, organisations may not apply the appropriate controls to non-corporate devices. At the same time, opportunistic cybercriminals are ramping up efforts to target vulnerable home workers. A threat which is compounded by the impact of reduced staffing levels in critical cyber security and IT teams.
The best way to prepare for these risks, is to ensure they are properly considered in your BCP. So, in the following infographic we explore 7 ways you can include cyber security in your business continuity plans - helping you respond to one risk, without creating another.
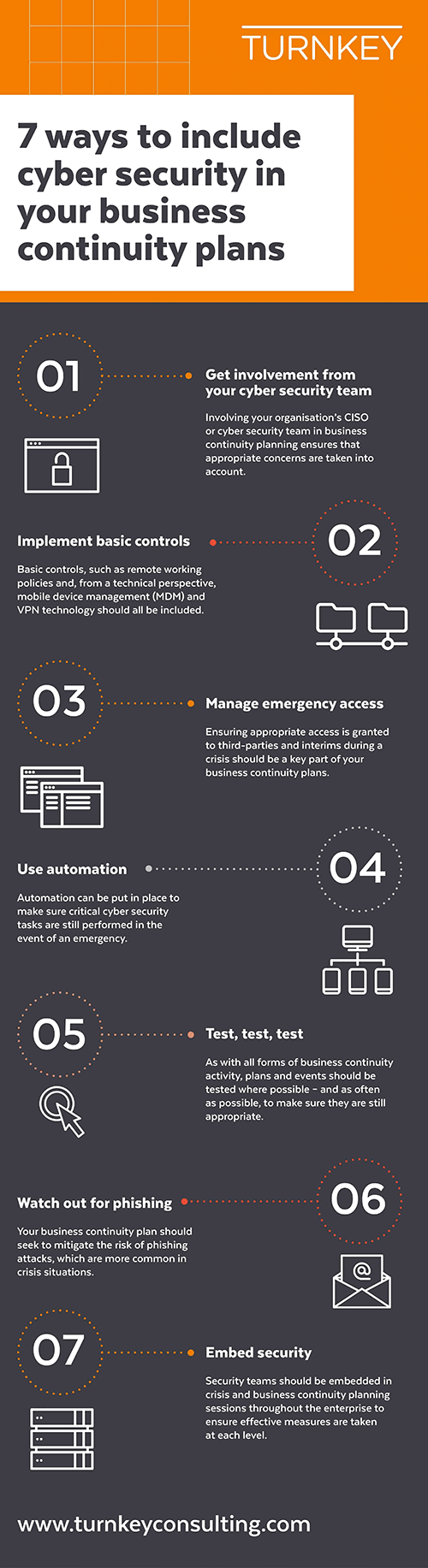
Below we give you an outline of 7 ways to include cyber security in your business continuity plans:
About Turnkey
Turnkey Consulting is helping to make the world a safer place to do business by specialising its expertise across Integrated Risk Management, Identity and Access Management, and Cyber and Application Security. We provide business consulting, technology implementation and managed services to help customers safeguard their application environments - protecting critical ERPs (such as SAP, Oracle and MS Dynamics) and wider enterprise systems.
