In today’s increasingly digital world, the security of critical business applications is a top priority for many organisations. Richard Hunt, Turnkey's founder and CEO, recently sat down with BizTechAsia to discuss what the cyber risk landscape looks like in 2023, and how Turnkey are helping to make the world a safer place to do business.
Richard kicked off the interview by exploring Turnkey's evolution from securing SAP systems for large organisations, to now providing a range of Integrated Risk Management (IRM), Identity & Access Management (IAM) and Cyber & Application security services for a number of businesses.
Walking through each of the practices, Richard explained how:
- Turnkey's IRM practice helps organisations to understand and define the business risk they face and unpack those risks into manageable components by developing risk responses and implementing control activities
- The IAM practice ensures that employees have the right access to systems at the right time and that access is removed when they leave the organization. We help provision the appropriate access, manage permissions and responsibilities, and ensure compliance with regulations
- As for the Cyber and Application Security practice, it helps clients secure their key business applications, particularly SAP systems, and manage cyber risks. This practice also provides training on cybersecurity awareness, ensuring that employees understand their role in managing risk and preventing cyber threats
The conversation then moved into the key risk management and cybersecurity trends for 2023, and Richard highlighted the geopolitical landscape changes we've seen in the past 12 months. These have had a direct influence on the cyber landscape due to cyber warfare, including state-sponsored actors targeting businesses.
Furthermore, he also mentioned the increasingly prominent role that AI is playing in cyber-attacks - and the need for businesses to stay alert to the various ways that automated attacks can manifest in organisations.
When risk is managed through self-assessment, facts and information in the risk management process are often omitted - which Richard stresses later in the interview. Organised crime has permeated the cybersecurity and ransomware space, with bad actors finding a new revenue stream in targeting companies.
As digitisation continues to reshape business processes, the need for secure critical business applications will only increase, making Turnkey Consulting's work even more critical as part of ensuring the safety of businesses and their customers.
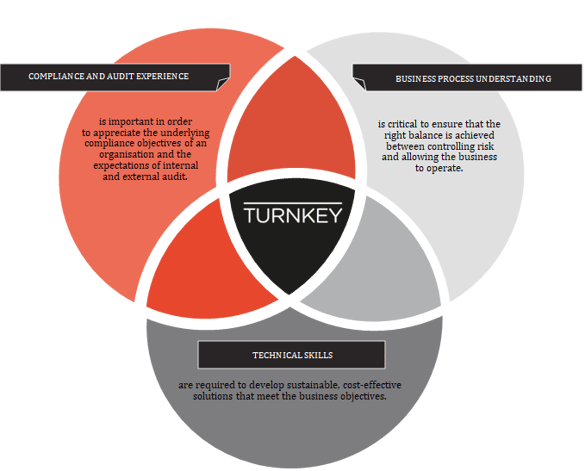
What sets Turnkey apart from larger consulting firms, Richard says, is a wealth of technical skills and a solid understanding of external audit and compliance requirements. With a foundational understanding of business processes, Turnkey consultants can identify the most appropriate control points, and put the right controls in place.
According to Richard, “We are a vendor-agnostic provider in terms of software products. We help customers to implement and then, get those projects right.” Ultimately, Turnkey’s ability to cover the entire Venn diagram of key areas necessary to solve problems for clients, as well as working closely with key partners, is what allows us to develop and implement solutions that meet our clients’ needs.
Richard's key advice for businesses facing evolving cyber threats is to prioritise cybersecurity awareness and risk management. A good start would be to place emphasis on:
- Addressing the basics, such as ensuring employees understand their personal responsibilities in managing risk
- Implementing solutions to protect wider and higher privileged access
- Managing cyber risks by focusing on identity management
By focusing on these key areas, and implementing good hygiene practices, businesses can improve their risk position and better protect themselves against cyber-attacks.
If you want to hear more of what was discussed, you can watch the full interview between Richard and Biztech Asia.
.jpg?width=1458&height=312&name=Turnkey%20Virtual%20Event%20Banner%20Template%202023%205-9-23%20(2).jpg)


