
Why do I need an Information Security Risk Assessment?
A systematic approach to information security risk management is necessary to identify organisational needs regarding information security requirements and to create an effective Information Security Management System (ISMS). Every organization is different and therefore, it is important that ISMS should be aligned with organization’s environment and specifically its enterprise risk management. The security effort should address risks in an effective and timely manner where and when they are needed. Risk assessment is the first process in any information security risk management program helps identify the relevant risks and the appropriate controls for reducing or eliminating these identified risks.
Risk assessment quantifies or qualitatively describes the information security risk and enables organisations to prioritise risks according to their seriousness. It determines the value of an information assets, identifies the applicable threats and vulnerabilities that exist (or could exist), identifies the existing controls and their effect on the risks identified, determines the potential consequences and finally prioritises them.
Our Information Security Risk Assessment (ISRA) methodology involves nine primary steps which helps in conducting an information risk assessment. The results provide inputs for your overall information security plan.
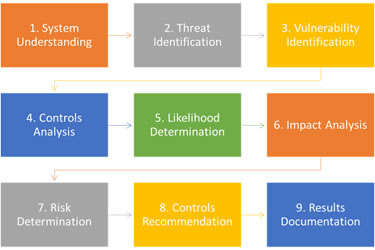
Our methodology is aligned with various industry standards such as ISO 27005.
Turnkey's ISRA methodology assists in applying the information security risk assessment process to identify risks associated with the loss of confidentiality, integrity and availability for information systems. It helps to focus information security efforts on areas of highest important to the organisation.

Turnkey's SAP GRC Managed Services help you ensure your SAP systems are secure with the latest SAP GRC tools and expertise. All delivered through the flexible and scalable Bedrock delivery model.
With Turnkey's SAP Security Managed Services, you get flexible access to both experienced onshore staff and highly-skilled offshore SAP security expertise - based in our Malaysia SAP Security Centre.